Explorer Cremit's intelligent features
Detect, alert, and remediate credential leaks automatically. Real-time protection powered by Argus
.svg)
.svg)
.svg)

Detect, alert, and remediate credential leaks automatically. Real-time protection powered by Argus
.svg)
.svg)
.svg)

.png)
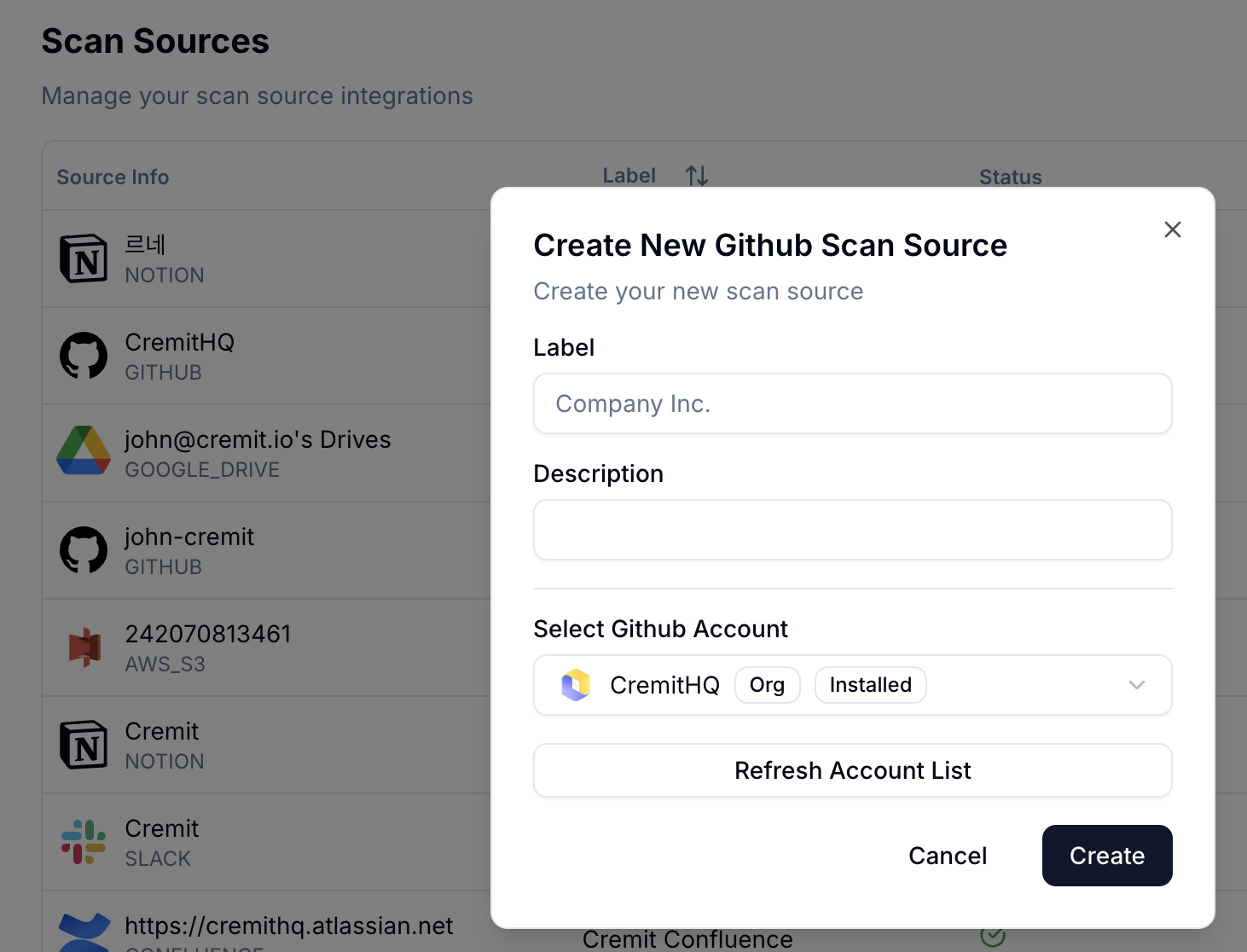
Integrate GitHub, Slack, Confluence, and your entire DevOps stack in minutes. Cremit instantly begins scanning for exposed secrets across 800+ credential types no agents, no complex setup, just immediate visibility.
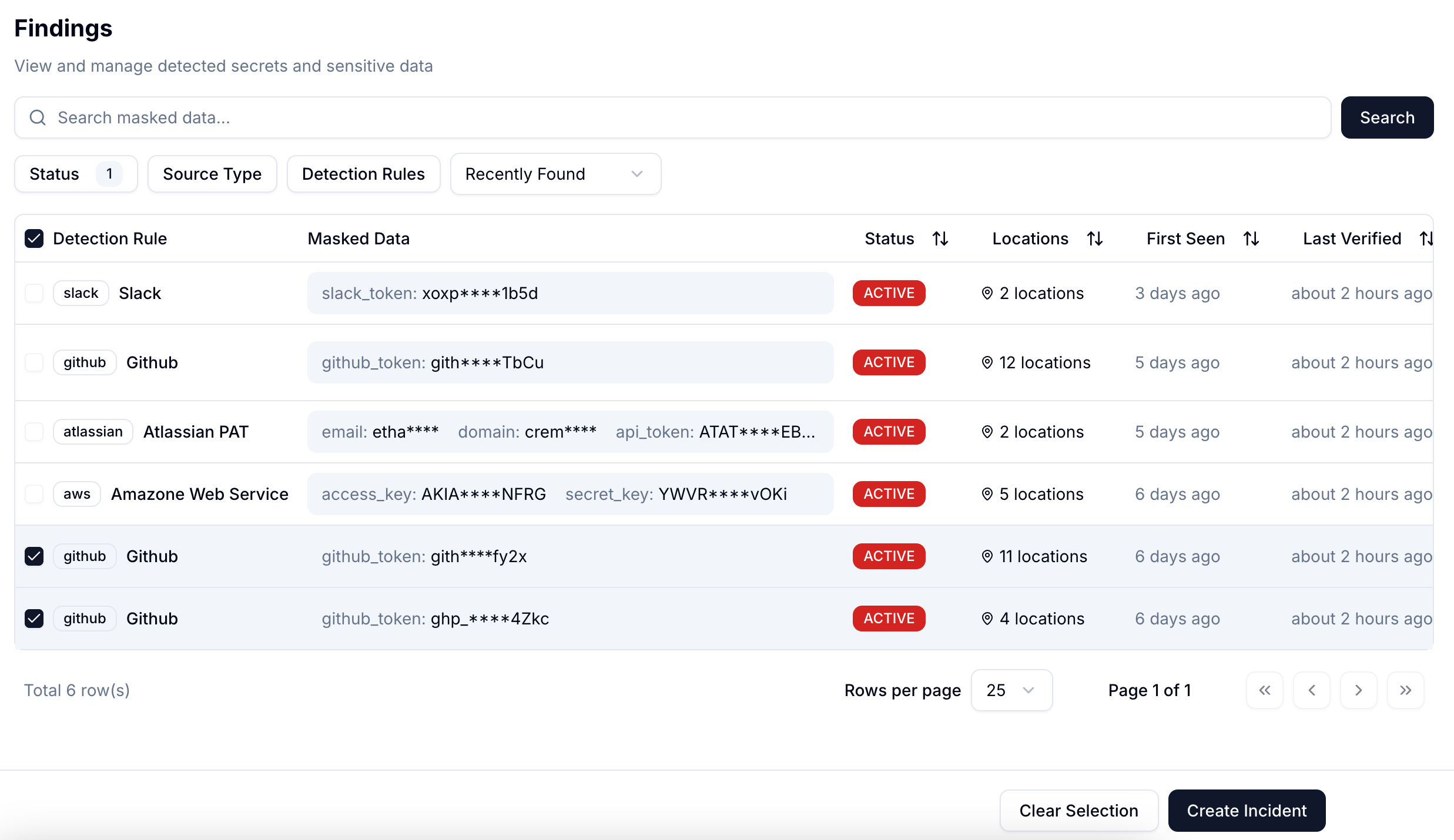
Turn every secret exposure into a tracked, actionable ticket. Cremit automatically creates issues in Jira, sends Slack notifications, and integrates with your existing incident management workflow—so your team can remediate fast without context switching.


Detect exposed API keys, tokens, and credentials the moment they're committed. Scan GitHub, GitLab, and Bitbucket repositories in real-time—before secrets reach production.



Find leaked credentials hidden in Slack messages, Confluence docs, and Jira tickets. Continuous monitoring across all collaboration tools where secrets accidentally get shared."



Rotate compromised credentials automatically with AWS Secrets Manager integration. Eliminate manual key rotation and reduce exposure windows from days to seconds. (Coming soon)



Stop wasting time on false positives. AI-powered risk scoring prioritizes critical exposures first, so your security team tackles real threats—not noise.



Get instant alerts with full context: what leaked, where it's exposed, and who needs to act. Delivered via Slack, email, or Jira with zero ambiguity.


Security that fits your workflow, not the other way around. Auto-generate GitHub PRs and Jira tickets without disrupting your dev team's velocity.


Still have questions?
We're here to help. Reach out to our team for answers about NHI security, implementation, or custom deployment options.
Cremit is an AI-powered Non-Human Identity (NHI) security platform that detects and prevents credential leaks in real-time. We scan 800+ types of secrets across GitHub, Slack, Confluence, and your entire tech stack—stopping breaches before they happen.
Unlike traditional tools, Cremit delivers 95% fewer false positives through advanced AI detection, supports 800+ credential types (including custom secrets), and provides seamless workflow automation with Jira 2-way sync and GitHub PR hooks.
Most teams are up and running in under 15 minutes. Simply connect your platforms (GitHub, Slack, etc.), and Cremit automatically begins scanning. No agents, no complex configuration required.
Absolutely. Cremit is ISO 27001 certified and SOC 2 ready. We maintain enterprise-grade security standards, and enterprise customers can choose dedicated regional deployments for data residency compliance.
