Build vs. Buy: Making the Right Choice for Secrets Detection
By
Felipe Araujo
November 17, 2025
4-minute read
By
Felipe Araujo
November 17, 2025
4-minute read
.png)
With cyber threats growing in sophistication and attack surface expanding, security teams face a pivotal decision: should you build custom security solutions in-house or invest in commercial platforms?
This decision is particularly crucial when it comes to Secrets Detection. Let's dive deep into what these solutions entail and explore the key factors that should guide your build-vs-buy decision.
Secrets like API keys, passwords, tokens, certificates, and other digital credentials, are the keys to your kingdom. They authenticate systems to one another and grant access to sensitive resources. As organizations embrace "everything-as-code" practices and complex cloud infrastructures, the volume of NHIs has exploded.
The risks are substantial. According to industry experts, poor secrets management can lead to devastating data breaches that pose existential risks to businesses. For large organizations with numerous developers using secrets daily across various environments, maintaining proper secrets hygiene becomes extraordinarily complex.
Building your own secrets detection solution offers several potential advantages:
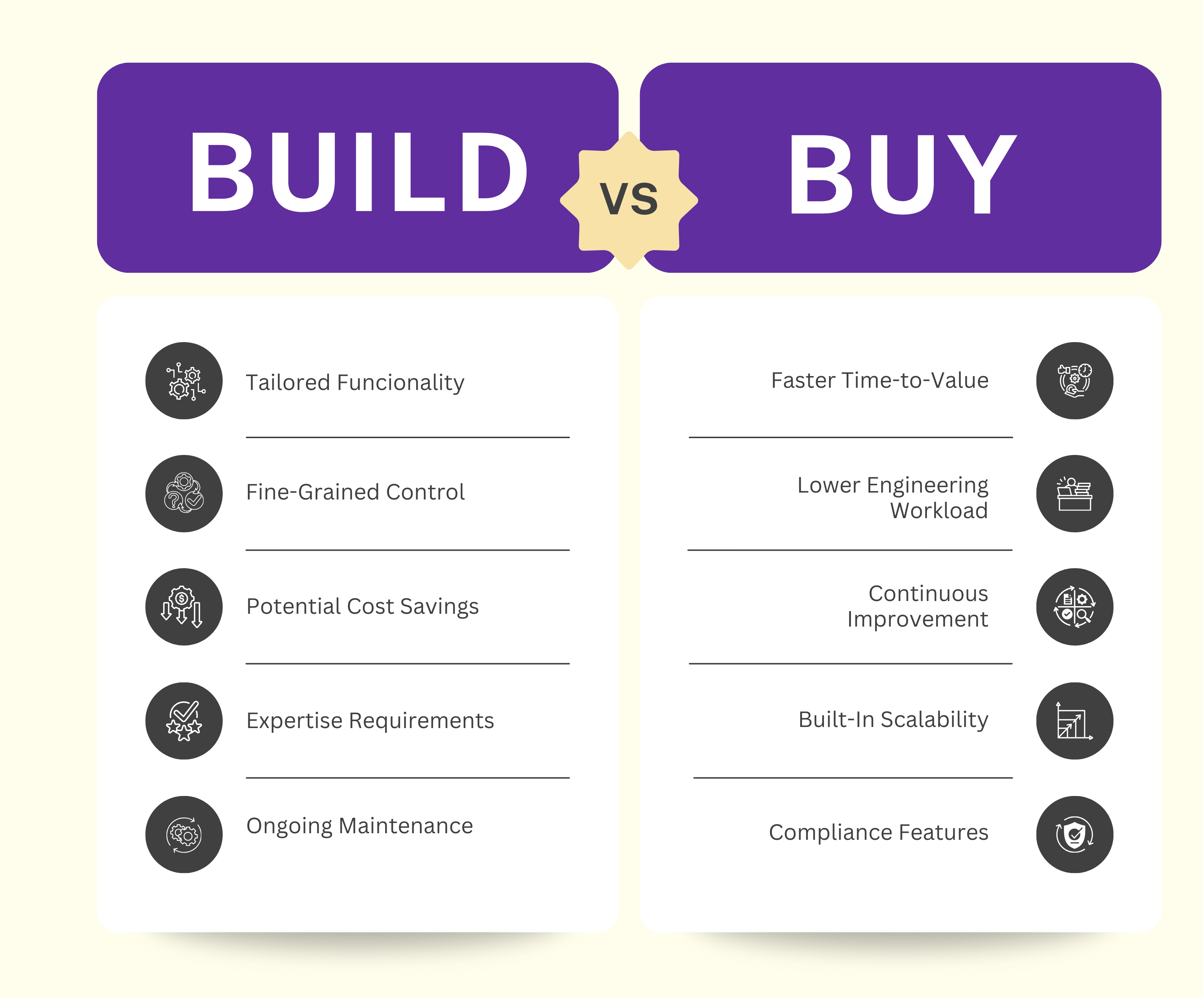
1. Tailored Functionality: Custom-built solutions can be designed to address your organization's specific security requirements and workflows.
2. Fine-Grained Control: Your team maintains complete control over the system's architecture, features, and integration points.
3. Potential Cost Savings: For organizations with unique needs and sufficient in-house expertise, building might appear less expensive than purchasing commercial licenses—at least initially.
Before committing to the build path, consider these significant drawbacks:
1. Development Time & Resources: Building a working secrets management system from scratch requires substantial time and skilled personnel, diverting valuable resources from core business initiatives.
2. Ongoing Maintenance Burden: As threats evolve and new vulnerabilities emerge, your team must continuously update and maintain the system—a never-ending commitment to expensive professionals.
3. Technical Debt: Homegrown solutions often accumulate technical debt that becomes increasingly difficult to manage over time.
4. Scaling Difficulties: As your organization grows, custom solutions require significant additional engineering effort to scale effectively.
5. Expertise Requirements: Building effective secrets detection solutions demands specialized knowledge across multiple domains, creating potential single points of failure within your team.
Commercial platforms for secrets detection offer compelling advantages that make them the preferred choice for most organizations:
1. Rapid Deployment & Faster Time-to-Value: Commercial solutions provide immediate access to cutting-edge technology, with deployment timelines measured in days or weeks rather than months or years.
2. Reduced Burden on Engineering Teams: Your developers can focus on building your core products instead of creating and maintaining complex security infrastructures.
3. Vendor Expertise & Continuous Improvement: Leading vendors continuously update their platforms with the latest security innovations based on research and real-world threat intelligence.
4. Built-in Scalability: Commercial solutions typically include autoscaling, load balancing, and multi-region support to grow with your organization needs.
5. Compliance Features: These tools usually have pre-built audit and compliance capabilities and certifications (like SOC 2, ISO 27001, etc.) that simplify meeting regulatory requirements.
Commercial solutions aren't perfect for every scenario:
1. Less Flexibility for Highly Specific Needs: Vendor platforms may not match custom-built systems for unique organizational requirements.
2. Vendor Dependencies: Your security practices may become tied to the vendor's development roadmap and support capabilities.
3. Ongoing Licensing Costs: Subscription fees continue as long as you use the solution.
When weighing build vs. buy for NHI Detection, evaluate these key considerations:
1. Scalability Requirements
Can your solution effectively handle increasing numbers of:
- Secrets and applications
- Users and access patterns
- Environments (on-premises, multi-cloud)
- Geographical regions
2. Security and Compliance Needs
Evaluate requirements for:
- Encryption standards and key management
- Compliance certifications (FIPS 140-2, SOC 2, ISO 27001)
- Security updates and vulnerability management
- Incident response capabilities
3. Total Cost of Ownership (TCO)
For building in-house, calculate:
- Development costs (engineering hours × hourly rate)
- Ongoing maintenance (typically 15-20% of development costs annually)
- Infrastructure costs
- Opportunity cost of diverting resources from core business
For commercial solutions, consider:
- Licensing fees
- Implementation costs
- Integration expenses
- Training requirements
4. Time-to-Value
How quickly do you need a working solution? Commercial platforms typically offer immediate value, while custom builds may take months or even years to reach feature parity.
5. Essential Features to Prioritize
Whether building or buying, ensure your solution includes:
- High accuracy with low (preferably zero) false positive rates
- Real-time scanning capabilities
- Integration with your development workflows and CI/CD pipeline
- Support for a wide range of secret types and programming languages
- Comprehensive reporting and alerting mechanisms
For most organizations, commercial solutions offer superior ROI for several compelling reasons:
1. Focus on Core Business: By purchasing a complete platform, organizations can allocate their internal resources to strategic initiatives that drive business growth.
2. Reduced Time-to-Security: Commercial solutions provide immediate protection, closing security gaps faster than custom development timelines allow.
3. Lower Total Cost of Ownership: When accounting for all costs—including development, maintenance, updates, and opportunity costs—commercial solutions often prove more economical in the long run.
4. Access to Specialized Expertise: Commercial vendors offer access to security researchers and domain experts that would be prohibitively expensive to maintain in-house.
5. Continuous Improvement Without Additional Investment: Vendors regularly enhance their platforms based on evolving threats and customer feedback, delivering ongoing value without requiring additional internal development.
Before making your final decision, consider conducting a formal proof of concept (POC) with potential vendors. An effective POC should:
- Provide initial results quickly (minutes, not days)
- Deliver actionable insights into your current security posture
- Demonstrate the platform's ability to integrate with your existing tools
- Help quantify the risks of not addressing security gaps
- Allow you to evaluate the vendor's support and expertise
While building custom security solutions might seem appealing for maximum control, the realities of today's threat landscape make commercial platforms like Cremit, the logical choice for most organizations.
The rapid deployment, scalability, and continuous improvement offered by specialized vendors typically deliver superior security outcomes while freeing your technical teams to focus on your core business objectives.
By carefully evaluating the factors outlined above, you can make a strategic choice that enhances your security posture while optimizing your resource allocation.
As you evaluate your organization's approach to secrets detection, remember that the right choice ultimately depends on your specific needs, resources, and security requirements.
If you've determined that a commercial solution aligns with your security objectives, we invite you to see how Cremit addresses the challenges discussed in this article. Experience firsthand how the right tools can enhance your security posture while freeing your team to focus on core business initiatives.
Ready to explore further? Schedule a demo with our security specialists, or contact us to begin the conversation about strengthening your application security strategy with solutions designed for today's complex threat landscape.
.png)
Need answers? We’ve got you covered.
Below are some of the most common questions people ask us. If you can’t find what you’re looking for, feel free to reach out!
We specialize in high-converting website design, UX/UI strategy, and fast-launch solutions for SaaS and startup founders.
Helping SaaS and startup founders succeed with conversion-focused design, UX strategy, and quick deployment.
Designing sleek, user-focused websites that help SaaS and startup teams launch faster and convert better.
We design and launch beautiful, conversion-optimized websites for ambitious SaaS and startup founders.
