Hidden Dangers: Why Detecting Secrets in S3 Buckets is Critical
By
Felipe Araujo
November 17, 2025
7-minute read
By
Felipe Araujo
November 17, 2025
7-minute read
.png)

Amazon S3 serves as the backbone of data storage for organizations of all sizes. With its unparalleled scalability, durability, and flexibility, S3 has become the default choice for storing everything from application assets to business-critical data. However, this widespread adoption comes with a significant security challenge that many organizations overlook until it's too late: exposed Non-Human Identities in S3 buckets.

Every day, sensitive credentials find their way into S3 buckets through various channels:
• Configuration files with hardcoded API keys
• Application logs capturing authentication tokens
• Database backups containing connection strings
• Developer uploads with unredacted sensitive information
• Third-party tool outputs containing access tokens
These exposed secrets—especially those belonging to Non-Human Identities (NHIs)—represent one of the most significant yet underaddressed security risks in cloud environments today. Unlike human user credentials, NHI secrets often possess extensive permissions, remain valid for extended periods, and lack the oversight that comes with human account management.
Non-Human Identity secrets deserve particular attention because they:
• Often have broader permissions than human accounts
• May not be subject to regular rotation policies
• Can persist in environments for months or years
• Lack direct human oversight and management
• Are frequently embedded in automated processes
• Can grant attackers wide-ranging access if compromised
Why Traditional Security Measures Fall Short
Many organizations believe their existing security controls adequately address this risk. However, traditional approaches have significant limitations:
While critical, preventative measures like these have inherent limitations:
• AWS Secrets Manager requires proactive adoption and doesn't address existing exposed secrets
• IAM Policies can restrict access but don't prevent credentials from being stored in files
• Bucket Policies control access to buckets but not the contents within files
• Developer Training helps but human error remains inevitable
Scale Makes Manual Detection Impossible
The mathematics of modern cloud environments make manual detection unfeasible:
• A typical enterprise maintains thousands of S3 buckets
• Each bucket may contain millions of objects
• Objects range from kilobytes to gigabytes in size
• New objects are constantly being created or modified
• Secrets can be buried deep within structured or unstructured data
Identifying exposed secrets amidst terabytes or petabytes of data presents significant challenges:
• Volume and Velocity: The sheer amount of data stored and the rate at which it changes make manual inspection impossible.
• Accidental Exposure: Secrets often land in S3 unintentionally – a developer pushes a config file with a hardcoded key, logs inadvertently capture sensitive tokens, or a snapshot includes live credentials.
• NHI Blind Spots: Finding service account keys or tokens used by applications and scripts requires specialized detection patterns.
• Limitations of General Tools: While native tools like Amazon Macie are valuable for identifying PII and certain common credential patterns, they might not catch all types of bespoke or application-specific secrets, or provide the focused workflow needed specifically for secret remediation.
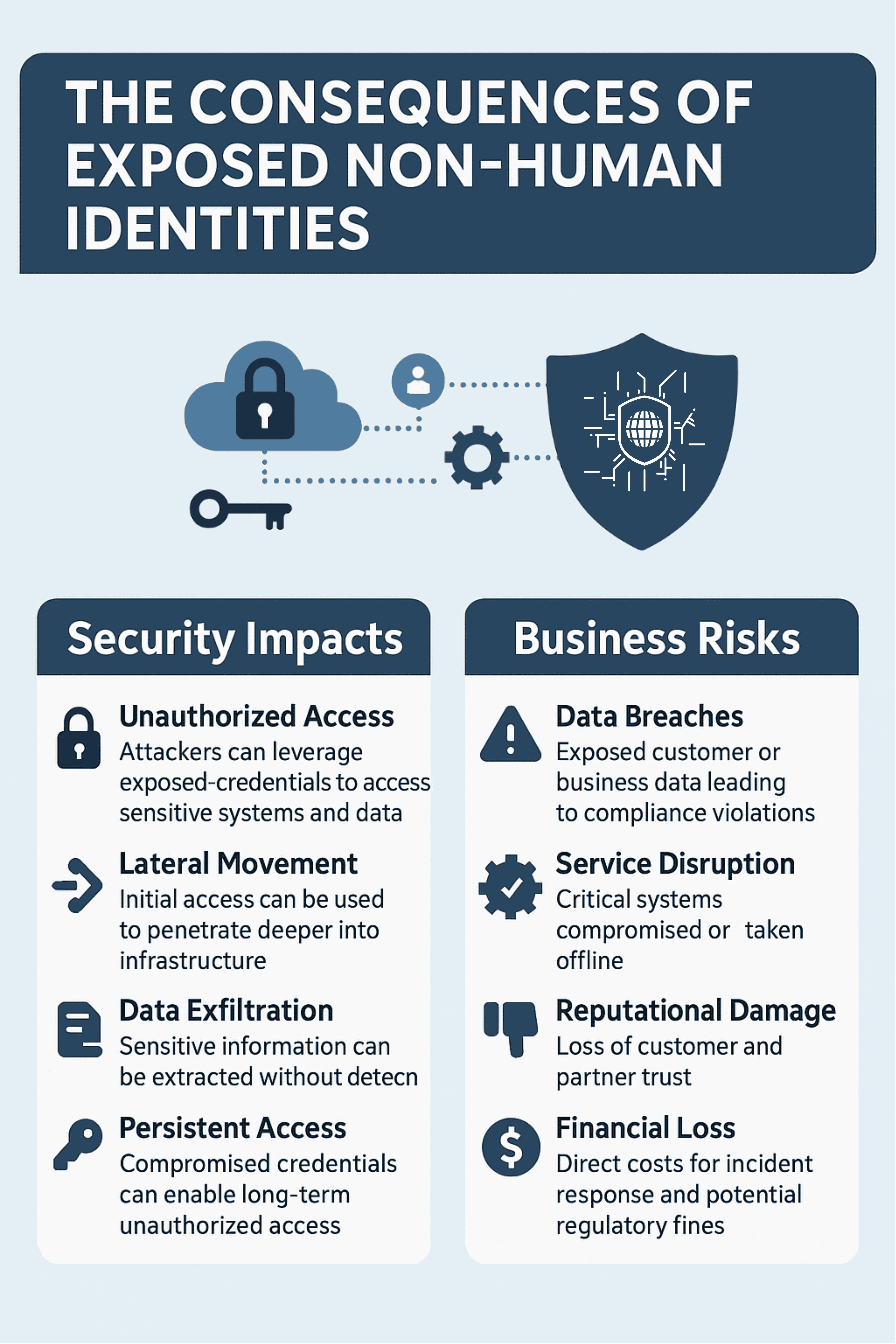
Proactive detection is the critical safety net. An effective detection strategy should include:
• Continuous Scanning: Automatic and regular scanning across all designated buckets
• Comprehensive Pattern Recognition: Identification of common credential formats and custom secret patterns
• NHI Credential Focus: Specialized detection for service account tokens, application keys, and all other NHI types
• Actionable Alerts: Clear, context-rich alerts that enable rapid investigation and remediation
False Positive Minimization: Intelligent filtering to reduce noise and focus on genuine threats
A holistic approach combines the preventative measures mentioned in your original document with robust detection:
• Enforce Least Privilege: Implement IAM Roles with tightly scoped permissions for all applications accessing S3
• Encrypt Data: Use SSE-S3 or SSE-KMS for data at rest and HTTPS for data in transit
• Monitor & Log: Employ CloudTrail (including S3 data events) and S3 Access Logs to track activity
• Automated Scanning: Regular scans of all S3 buckets
• Multi-Pattern Detection: Recognition of various secret types
• NHI Credential Focus: Specialized detection for service accounts
• Risk-Based Prioritization: Focus on high-impact findings first
• Integration with Security Workflows: Connect findings to remediation processes
• Immediate Notification: Alert security teams when secrets are discovered
• Rapid Remediation: Quickly revoke and replace exposed credentials
• Root Cause Investigation: Identify how the secret was exposed to prevent recurrence
When evaluating solutions for secret detection in S3, organizations should consider tools specifically designed for this purpose. Cremit is designed to provide continuous, targeted detection of secrets, including sensitive NHI credentials, within Amazon S3 buckets.
Key capabilities to look for in a dedicated solution include:
• S3-Specific Scanning: Technology optimized for the unique characteristics of S3 environments
• Comprehensive Secret Detection: Ability to identify numerous credential types across multiple file formats
• NHI Credential Expertise: Specialized patterns for machine identities and service accounts
• Integration Capabilities: Seamless connection with existing security workflows
• Remediation Guidance: Clear direction on addressing discovered secrets
Don't wait until a security incident reveals exposed secrets in your S3 environment. Proactive detection is essential for identifying and addressing this critical vulnerability before it can be exploited. By implementing both strong preventative measures and robust detection capabilities, organizations can significantly reduce the risk posed by exposed secrets in their S3 buckets.
Cremit is designed to address the critical challenge of exposed secrets in S3 buckets. Our platform provides:
• Proactive Discovery: Continuous scanning to find exposed secrets across your entire S3 landscape before they can be exploited
• NHI Credential Detection: Identification of high-risk Non-Human Identity credentials that could grant attackers extensive access to your environment
• Actionable Insights: Clear, context-rich information that enables your security team to quickly remediate findings
• Seamless Integration: Easy connection with your existing security workflows to streamline the remediation process
Ready to secure your S3 environment?
Contact us to discover how our purpose-built S3 secret detection platform can help you.
Don't let exposed secrets in S3 be your organization's Achilles' heel. Take the first step toward comprehensive S3 security today.
.png)
Need answers? We’ve got you covered.
Below are some of the most common questions people ask us. If you can’t find what you’re looking for, feel free to reach out!
We specialize in high-converting website design, UX/UI strategy, and fast-launch solutions for SaaS and startup founders.
Helping SaaS and startup founders succeed with conversion-focused design, UX strategy, and quick deployment.
Designing sleek, user-focused websites that help SaaS and startup teams launch faster and convert better.
We design and launch beautiful, conversion-optimized websites for ambitious SaaS and startup founders.
