API Keys Traded on the Dark Web: Hackers' New Target
By
Ben Kim
December 26, 2025
8 min read
By
Ben Kim
December 26, 2025
8 min read
.png)
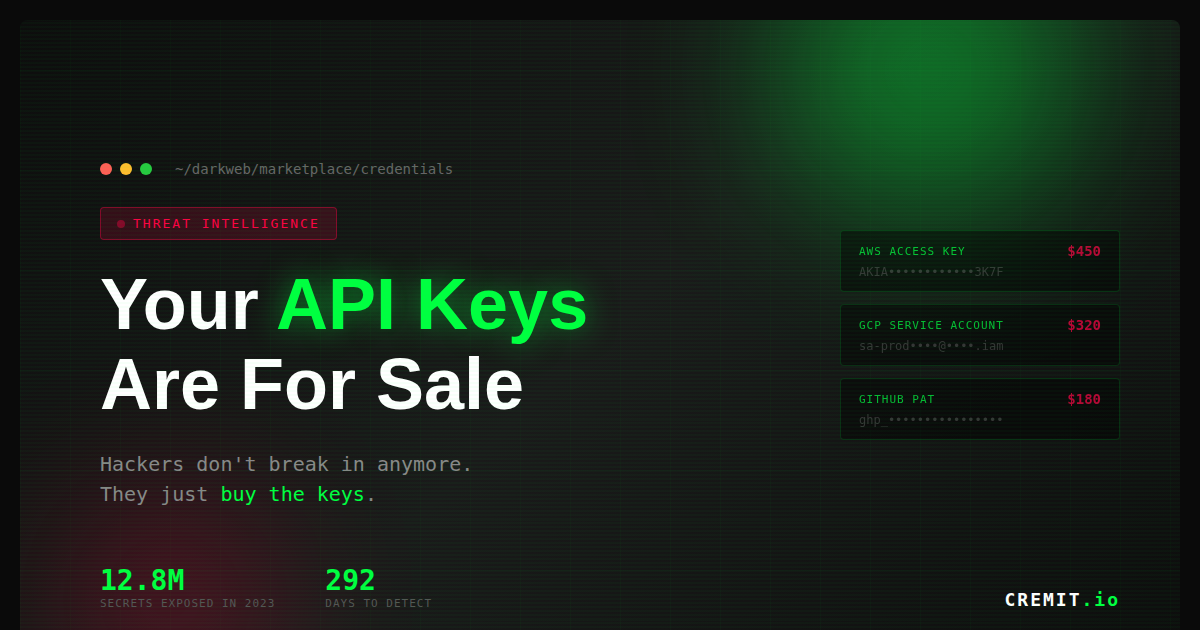
API Keys are being traded on the dark web. Hackers no longer bother with complex techniques to breach firewalls—they simply buy the 'keys.' This article explores why insider threats and Non-Human Identity (NHI) security have become critical in the cloud and AI era, and why continuous internal monitoring is now essential.
API Keys are being traded on the dark web.
Hackers no longer bother with complex techniques to breach firewalls. They simply buy the 'keys.' AWS Keys accidentally committed to GitHub, service account credentials shared on Slack, API tokens left on a former employee's laptop. All of these are priced and traded on the dark web. A single leaked API Key grants access to systems through legitimate channels—no complex intrusion required.

According to Verizon's 2024 Data Breach Investigations Report, 74% of all data breaches involve the human element, with a significant portion linked to credential theft. IBM's Cost of a Data Breach Report 2024 reveals that breaches caused by stolen credentials take an average of 292 days to detect. That means attackers can operate freely inside systems for nearly 10 months.
This is the reality of today's security threat landscape.
The perimeter has dissolved. In a world of remote work, cloud infrastructure, and AI agents, trusting based on network location is no longer possible.
As the cloud and AI era accelerates, the fundamental premises of enterprise security are shifting. In the past, the boundary between 'inside' and 'outside' was clear. Security strategies focused on perimeter defense, trusting everything inside the firewall while treating everything outside as a threat.
But that boundary has become meaningless.
Employees access business systems from anywhere through remote work. Critical data is distributed across public clouds like AWS, GCP, and Azure rather than on-premises infrastructure. SaaS applications interconnect via APIs, making data flows between systems increasingly complex. AI agents and automation bots traverse systems without human intervention.
Gartner projected that 85% of enterprise workloads would run in the cloud by 2025. For most organizations, the concept of an 'internal network' has already faded. Determining trust based on whether an IP address is internal or external is simply no longer possible.
In this environment, the traditional security paradigm of 'blocking external intrusions' inevitably hits its limits.
The fundamental challenge with insider threats is that they involve actions by individuals with legitimate access. The system cannot distinguish between normal work and malicious intent.
Insider threats have long been considered the most difficult security challenge to address. The fundamental difficulty lies in the fact that these are actions by 'individuals with legitimate access.'
External attacks can be blocked with firewalls, intrusion detection systems, and multi-factor authentication. However, when employees with authorized system access query and use data, distinguishing this from normal work is nearly impossible. A sales representative querying customer information, a developer accessing a production database—these actions could be legitimate business needs or malicious intent. From the system's perspective, both actions look identical.
According to Ponemon Institute's 2023 Cost of Insider Threats Global Report, the average cost per insider threat incident is $15.4 million—a 34% increase from 2020. Even more concerning, it takes an average of 86 days to contain an insider threat incident. And the frequency is rising. The same report indicates insider threat incidents increased 44% over the past two years.
Another characteristic of insider data breaches is that no abnormal traffic is generated. Even when hundreds of thousands of records are exfiltrated, if they're logged as 'normal queries,' security solutions won't raise alerts. This is why most insider breaches are discovered months, sometimes years, after the fact—often through external tips or law enforcement notifications.
CISA (Cybersecurity and Infrastructure Security Agency) defines insider threats as "current or former employees, contractors, or business partners with authorized access to organizational assets who misuse that access to negatively impact the confidentiality, integrity, or availability of critical information or systems." The key phrase here is 'authorized access.' This is what makes insider threats so fundamentally difficult to prevent.
Non-Human Identities now outnumber human users by 10 to 50 times. These machine identities carry the same vulnerabilities as human insiders—and in some ways, they're even more dangerous.
There's another trend demanding attention: security threats are expanding from 'humans' to 'machine identities.'
NHI (Non-Human Identity) refers to credentials used for system-to-system communication, including API Keys, service accounts, bot tokens, OAuth tokens, certificates, and microservice authentication information. As organizations transition to cloud-native environments, the number of NHIs has exploded.
The scale is staggering. Industry analysis estimates that NHIs typically outnumber human user accounts by 10 to 50 times in enterprise environments. Large organizations may have hundreds of thousands of API Keys and service accounts. The problem is that many of these remain unmanaged.
According to CyberArk's 2024 Identity Security Threat Landscape Report, 93% of organizations experienced two or more identity-related breaches in the past year. And 68% of security leaders identified managing non-human identities as their biggest challenge. This isn't theoretical concern—it's a realized threat.
The AI era is accelerating this trend. LLM-based agents use API Keys to communicate with external services, and automation workflows connecting multiple systems are driving exponential growth in service accounts. As standards like MCP (Model Context Protocol) spread, AI agents are accessing an ever-wider range of systems. A single AI agent connecting to dozens of external services has become routine.
The problem is that these NHIs carry the same security vulnerabilities as human insiders. In some ways, they're even more dangerous.
First, NHIs don't take vacations. They exist in an active state 24/7/365. Once leaked, attackers can access them anytime.
Second, NHIs are often granted excessive permissions. Broad access rights are frequently set for development convenience and rarely adjusted to follow least-privilege principles afterward.
Third, NHIs often never expire. It's common for API Keys to be used for years without rotation. OWASP (Open Web Application Security Project) lists this as one of the top API security risks.
Fourth, NHI ownership is often unclear. The developer who originally created a key leaves the company, and no one knows where or how that key is being used—'unmanaged keys' are left scattered throughout the organization.
An API Key is an 'identity' granted legitimate access to systems. When that key is leaked, attackers can access systems from outside as if they were internal systems. No need to breach firewalls. No need to bypass authentication.
Why attempt difficult hacks when you can simply buy leaked keys? Trading API Keys and credentials on the dark web has become an industry.
Hackers have already figured this out. And they're rational. Why attempt difficult hacks when you can simply buy leaked keys?
Trading API Keys and credentials on the dark web has become an industry.
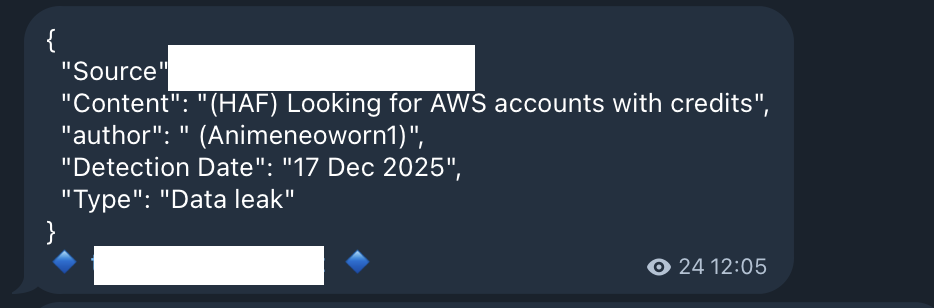
Leak vectors are diverse.
API Keys accidentally committed to code repositories like GitHub and GitLab are the most common path. According to the 2024 State of Secrets Sprawl Report, 12.8 million new secrets were detected in public GitHub repositories in 2023 alone—a 28% increase year-over-year. Tens of thousands of API Keys are accidentally exposed in public repositories every day.
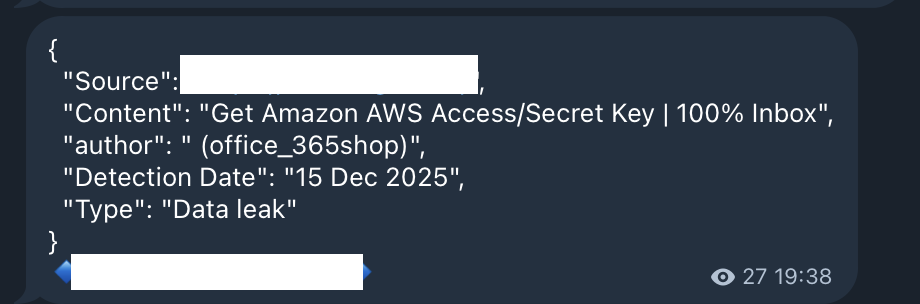
Credentials shared in collaboration tools like Slack, Confluence, and Notion are another major leak vector. Test account information shared in channels for convenience, service account passwords documented in wikis—all become attack targets.
Inadequate offboarding management is also serious. API tokens left in former employees' local environments, configuration files backed up to personal clouds—all flow into the dark web. The bigger problem is when API Keys created by departed employees remain active after they leave. The owner is gone, but the key still works. This is the reality for many organizations.
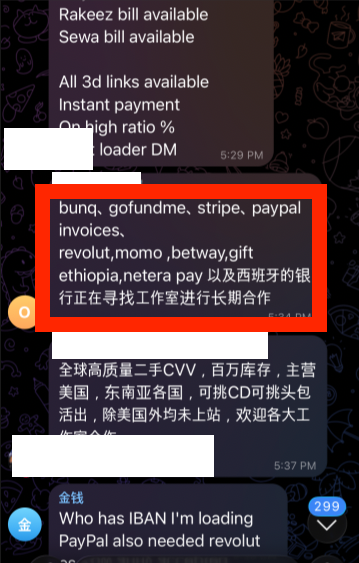
Tokens logged in plaintext, environment variables captured in screenshots, even real API Keys included in Stack Overflow questions—attackers monitor all these vectors.
From an attacker's perspective, leaked API Keys are extremely attractive assets. They enable access through legitimate authentication paths without complex hacking techniques. Access gained through such keys is indistinguishable from normal traffic. It's essentially the same situation as an insider querying data with legitimate permissions.
Security teams have no way to distinguish whether this is an external attack or normal internal system operation. In cloud environments especially, determining internal versus external based on IP addresses alone is impossible. Attackers exfiltrate data through normal API calls, and the logs record nothing but 'normal requests.'
These aren't theoretical threats. Major breaches from credential leaks have already occurred—and the common thread isn't sophisticated zero-day exploits, but simply leaked or over-permissioned credentials.
This isn't theoretical. Major security incidents from API Key and credential leaks have already occurred multiple times.
In 2023, an AI research team at a global tech company accidentally exposed 38TB of internal data while sharing AI models on GitHub. The cause was a shared token with excessive permissions.
A CI/CD platform provider experienced a security breach in early 2023 and had to advise customers to rotate all stored secrets. Attackers had accessed customer environment variables and API Keys through internal systems.
In 2022, a major mobility company was infiltrated through credentials an attacker presumably purchased on the dark web. The hacker used social engineering to bypass MFA, but the initial access vector was leaked credentials.
What do these cases have in common? They weren't complex zero-day vulnerability exploits. Already-leaked or overly-permissioned credentials were the starting point for each attack.
Zero Trust isn't just a buzzword. When threats come from identities with legitimate access, you must verify every request continuously—regardless of network location.
Ultimately, threats from 'identities with legitimate access'—whether human or machine—cannot be stopped by traditional perimeter security alone. In an environment where the perimeter itself has vanished, focusing solely on 'blocking external intrusions' is no longer a valid strategy.
NIST's Zero Trust Architecture (SP 800-207) reflects this environmental change. The principle states: "Trust should not be implicitly granted, and all access requests must be continuously verified." This means access control based on identity and context, not network location.
Security perspectives must now expand to 'internal anomaly detection.' The reasons for internal monitoring are clear.
First, understand the 'context' of authorized access. Beyond simply knowing who accessed what data, analyze whether patterns differ from normal, whether access occurred outside business hours, whether unusually large data volumes were queried, or whether previously unused APIs were called. Even with the same API Key, access from unusual locations, at irregular times, or with abnormal call frequencies could indicate a leak.
Second, manage the entire NHI lifecycle. Continuously track when API Keys were created, by whom, where they're currently used, what permissions they have, and which keys are no longer needed. Many organizations have API Keys created years ago still active with excessive permissions. The developer who created them has left, and no one knows which system uses them—these 'unmanaged keys' are golden opportunities for attackers.
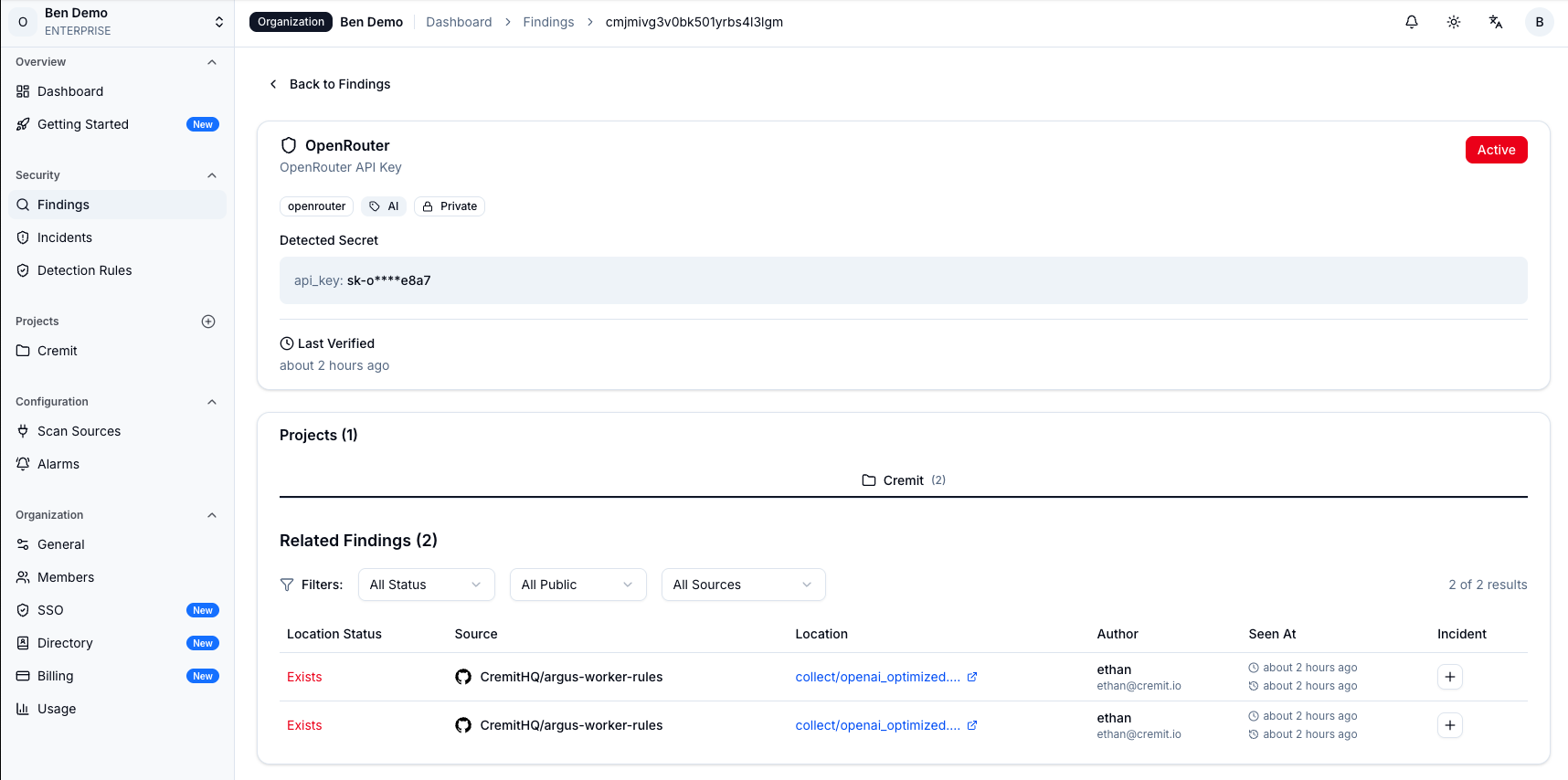
Third, establish real-time detection and response systems. Rather than learning about breaches months later, receive alerts immediately when credentials are exposed externally or anomalies are detected, enabling swift action. If the 292-day detection time from the IBM report can be reduced to days or hours, damage can be dramatically minimized.
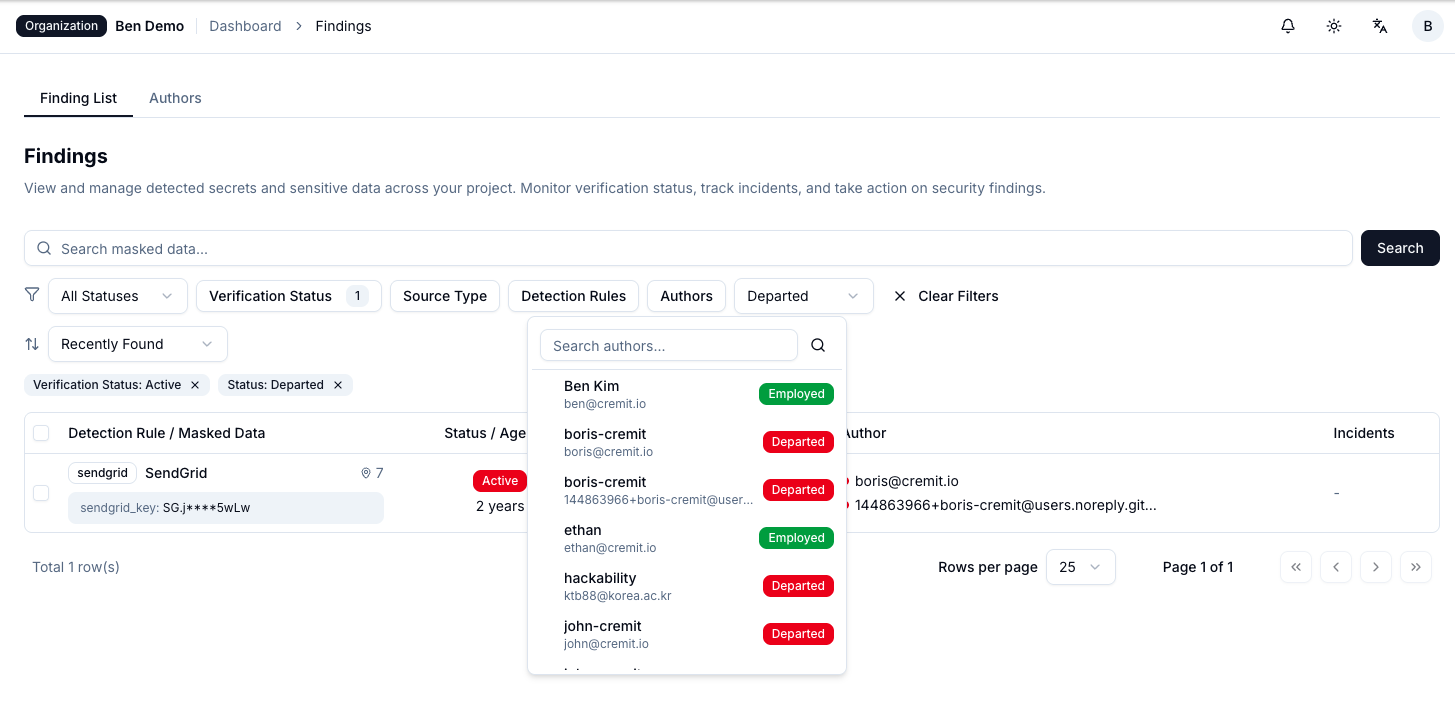
Fourth, proactively detect credential exposure. Continuously monitor whether your organization's API Keys or credentials have been exposed in public repositories like GitHub, on the dark web, in pastebin sites, and elsewhere. You must discover and respond before attackers exploit them.
Fifth, systematically manage offboarding-related risks. When employees leave, identify all credentials they created or accessed and take necessary action. Simply deactivating accounts isn't enough. Verify whether API Keys, service accounts, and access tokens they created are still valid, then rotate or revoke them.
Cremit's Argus platform provides comprehensive NHI security—from real-time leak detection to lifecycle management and offboarding risk assessment.
This is precisely the problem Cremit aims to solve.
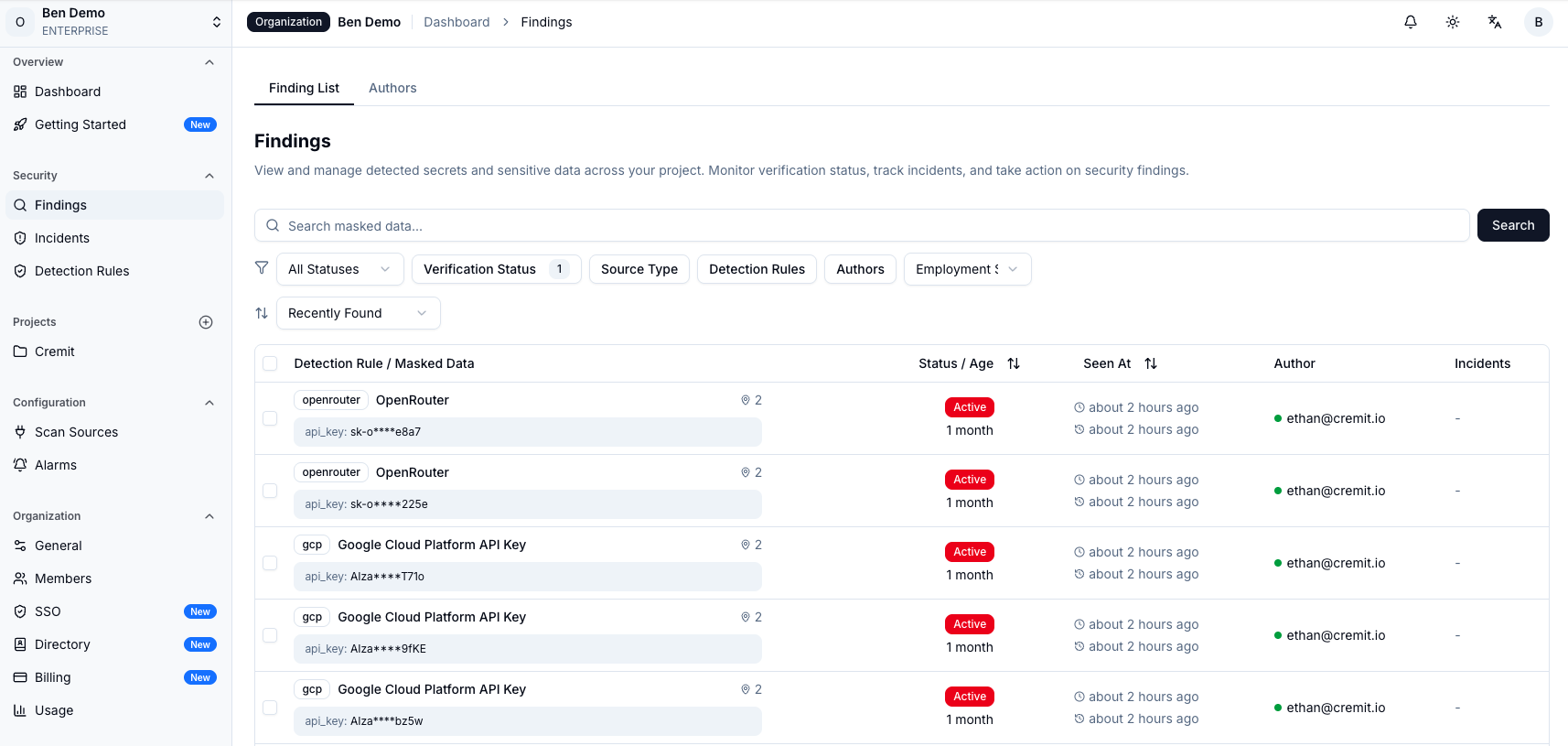
Cremit's Argus platform monitors organizational NHIs in real-time and detects credential leaks using an advanced detection engine. It provides integrated scanning across development and collaboration environments including GitHub, GitLab, Slack, Confluence, and Jira, supporting over 800 secret types.
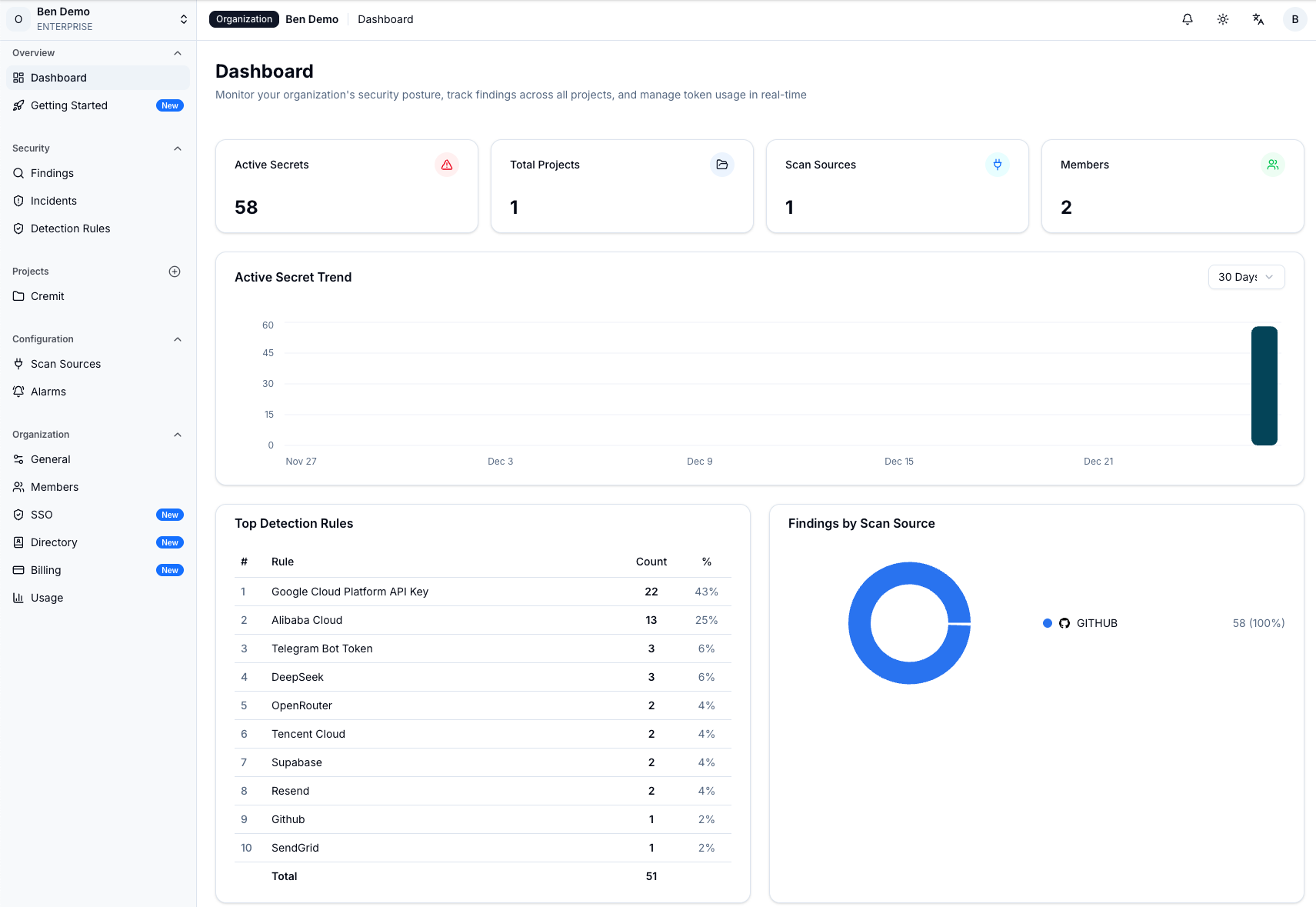
Cremit's advanced detection engine performs context-based analysis beyond simple pattern matching. It accurately distinguishes whether detected credentials are actually valid, test dummy data, or already expired keys—reducing false positives by over 95%. This prevents security teams from drowning in hundreds of false positive alerts while missing actual threats.
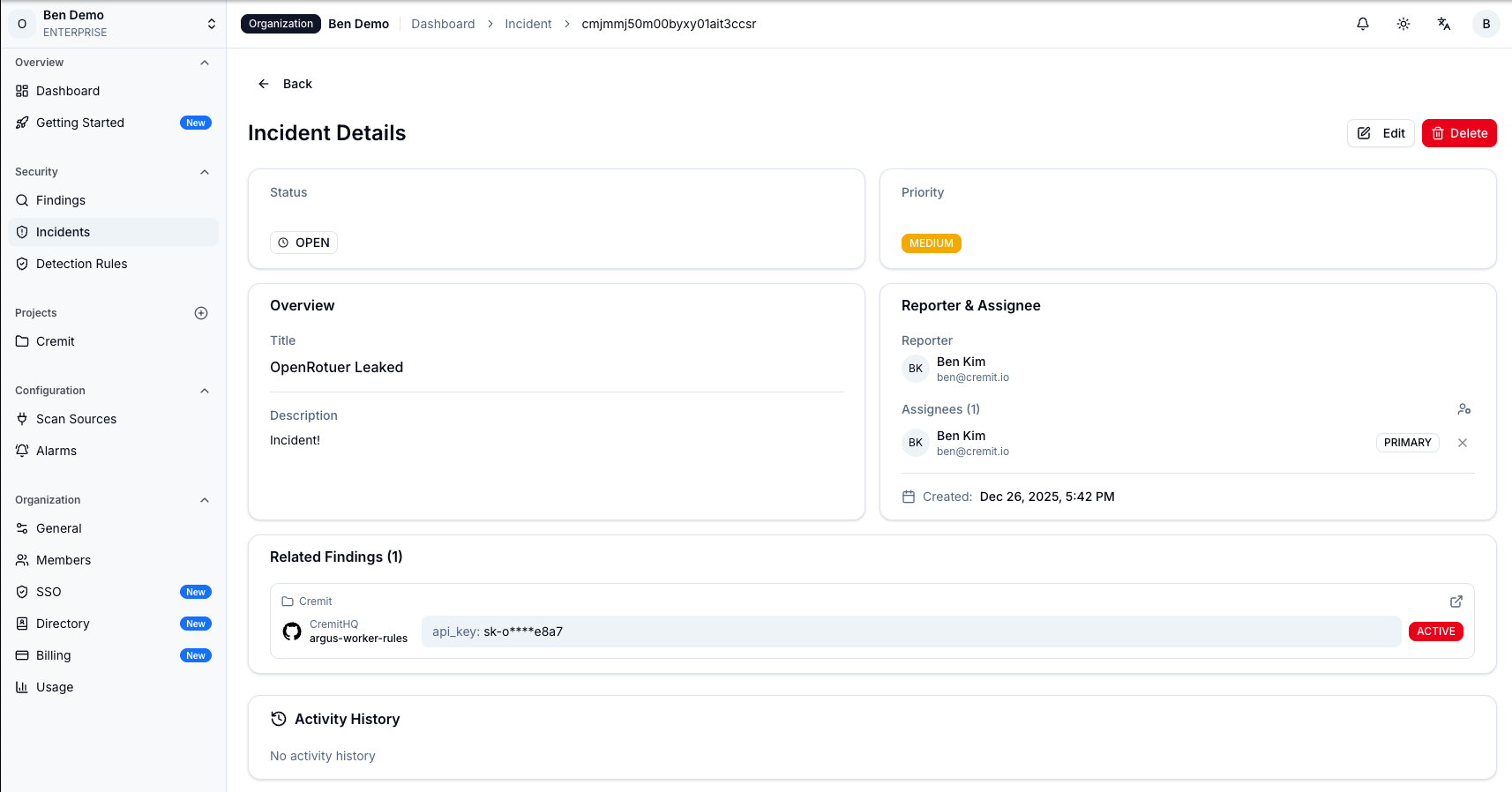
When credentials are detected, real-time alerts are sent along with context information (creation time, creator, usage location, permission scope, etc.) to enable rapid response. The platform also tracks the entire NHI lifecycle to proactively identify potential risks like unmanaged keys and service accounts with excessive permissions.
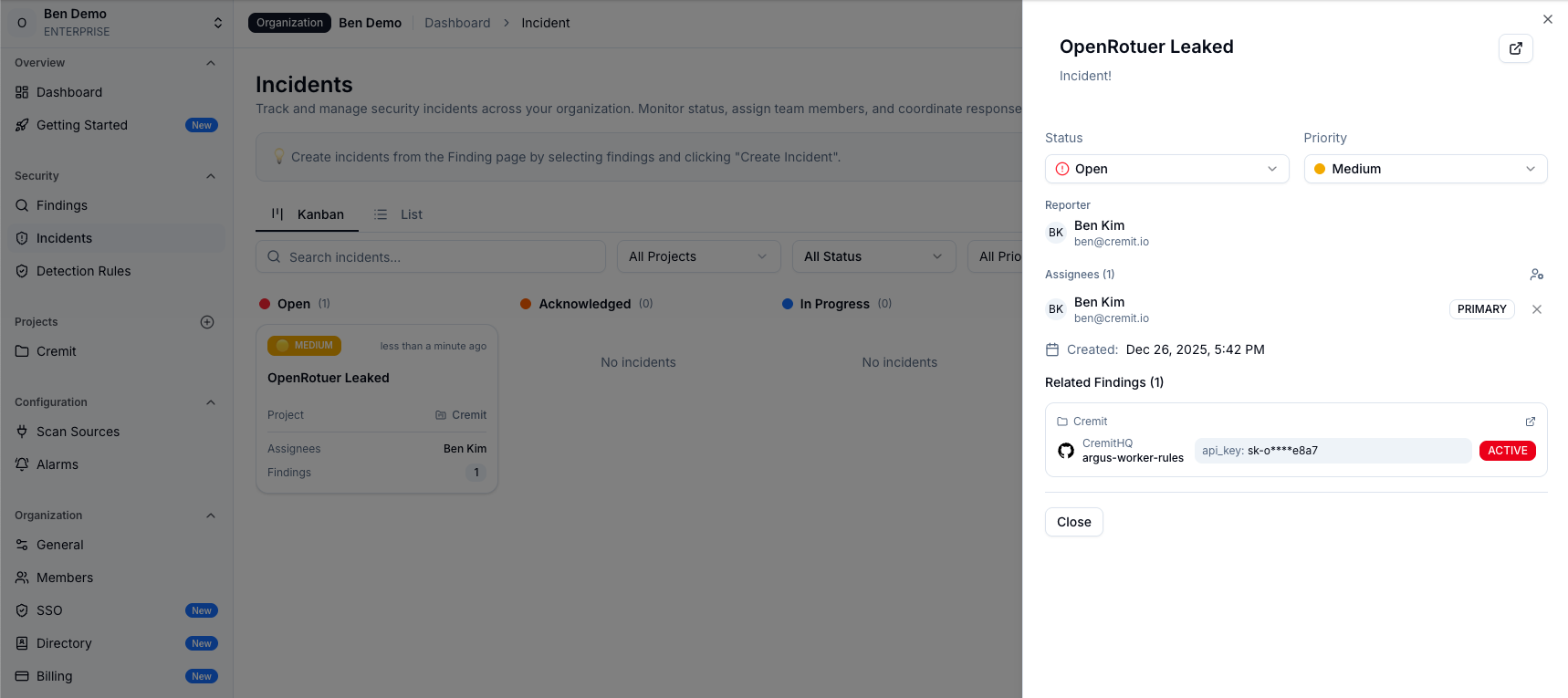
Cremit recently updated its offboarding risk management feature. By integrating with HR systems, it automatically identifies all NHIs associated with departing employees, assesses risk levels, and recommends necessary actions. API Keys created or last used by departing employees, service accounts known only to them—credentials at risk of becoming 'unmanaged' can be identified and addressed proactively.
Conclusion: Protecting Keys Keeps Doors Secure
No matter how strong you make the door, it's useless if the keys are being copied and passed around. It's time to manage the keys.
In the cloud and AI era, the fundamental premises of security have changed. The dichotomy of 'safe inside' versus 'dangerous outside' no longer holds. Hackers have already recognized this shift and transitioned from breaching firewalls to buying keys.
The countless API Keys, service accounts, and AI agents throughout organizations carry the same risks as traditional insider threats—perhaps even greater. No matter how thoroughly you defend external perimeters, you cannot stop threats moving with legitimate internal access.
No matter how strong you make the door, it's useless if the keys are being copied and passed around. It's time to manage the keys.
Gaining visibility into both human and machine identities with continuous monitoring—this is why it has become a mandatory requirement for modern security.
Is your organization's API Key already being traded on the dark web?
Is an API Key created by a former developer still working in production?
Assess your NHI security posture with Cremit.
👉 Request a free demo at cremit.io
Table of Contents:
.png)
Need answers? We’ve got you covered.
Below are some of the most common questions people ask us. If you can’t find what you’re looking for, feel free to reach out!
We specialize in high-converting website design, UX/UI strategy, and fast-launch solutions for SaaS and startup founders.
Helping SaaS and startup founders succeed with conversion-focused design, UX strategy, and quick deployment.
Designing sleek, user-focused websites that help SaaS and startup teams launch faster and convert better.
We design and launch beautiful, conversion-optimized websites for ambitious SaaS and startup founders.
