Customer Interview: Insights from ENlighten
By
Ben Kim
November 17, 2025
4-minute read
By
Ben Kim
November 17, 2025
4-minute read
.png)

We had the pleasure of interviewing Jinseok Yeo from ENligthen, Korea’s leading energy IT platform. In this conversation, we explored how ENligthen has implemented commitments and kept credentials and secrets secure. Let’s dive into their journey and discover their innovative approach!

We are a company that creates value beyond connection by gathering more energy, more powerful energy. By connecting scattered renewable energies with IT technology, we are implementing a platform trading platform where supply and consumption can be freely exchanged. Currently, we provide online business feasibility review services and reliable asset management services to power generators using the platform, RE100 consulting and power trading services to companies that need renewable energy electricity, and have signed power purchase agreements (third-party PPAs) with NAVER New Building and Lotte Global Logistics. ENLighten's power generation king service is the largest single service in Korea, with more than 22,000 locations nationwide and more than 5.4 GW of power plants connected, and a market share of 25%.
Enlighten operates services such as solar integration business, energy IT platform, and VP platform for energy trading. It is the No. 1 energy platform company in Korea that is innovating the energy market with its outstanding technology and expertise. With KRW 44.5 billion in cumulative investment, 5,344MW in total service volume, and the most used platform by power producers, we have a team with years of experience from diverse backgrounds including Seoul National University, UC Berkeley, EY, Mirae Asset, Samsung Electronics, and Tada.

Attackers are constantly scouring public code repositories like GitHub for accidentally exposed secrets, such as credentials and API keys. Even minor mistakes, such as sharing secrets in internal messaging or collaboration tools, can create vulnerabilities that attackers may exploit.
Like many companies, we struggled with detecting and managing secrets and credentials across repositories, collaboration tools, and messaging platforms due to a lack of specialized solutions. That’s why we quickly chose Cremit. Its low cost, real-time detection and notifications, intuitive dashboard for at-a-glance status updates, and seamless integration made it an obvious choice.
One of the fundamental features of Cremit for us are both the Secret and Sensitive Tables, which gives us an overview of where our credentials are exposed. In addition to showing us where a secret key is exposed, Cremit also tells us if the secret is active, so we can prioritize our actions. I open a ticket to the development team or other members who need to know which secret and credential values are active and take action based on where they are exposed.
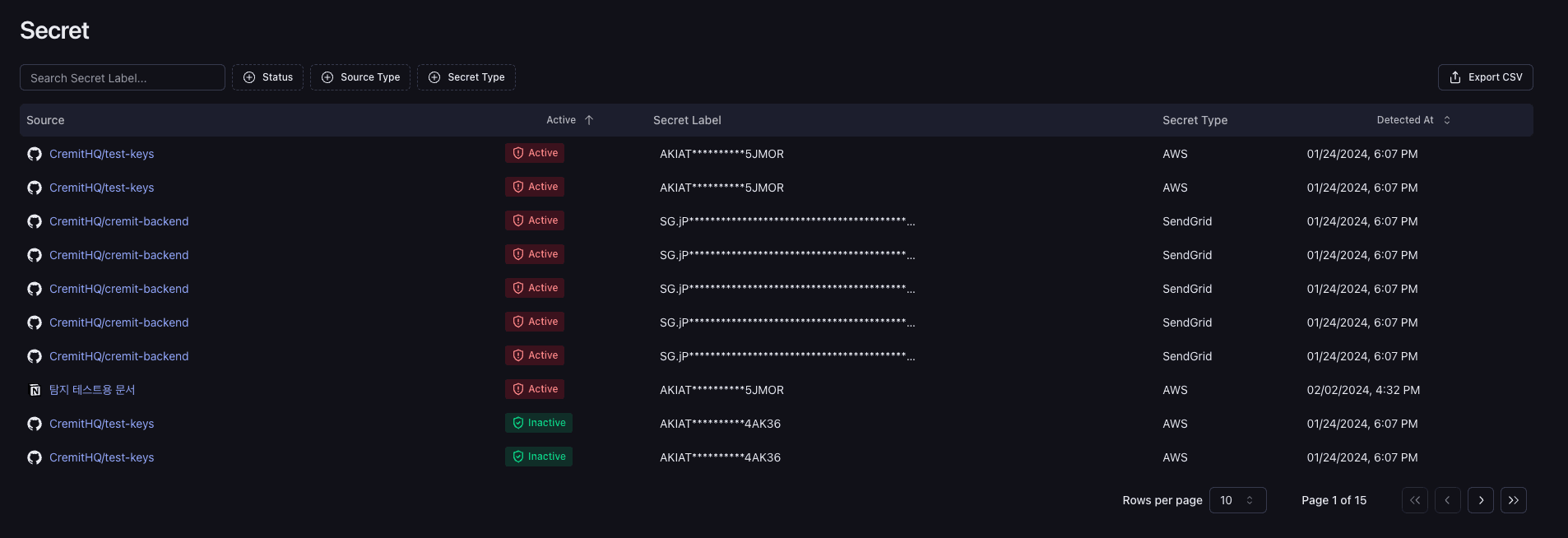
I especially like the fact that since the introduction of Cremit and its NHI Traceability, we can find sensitive secrets in source codes that were developed in the past but were not being maintained, clean them up, find the origin, and find improvement points. Also, the intuitive dashboard allows me to see what's going on, which is very helpful in improving the security of Enlighten.
We are committed to actively leveraging Cremit to support our developers, secure the services our members deliver to their customers, and identify outdated credentials no longer in use. Additionally, we will continue enhancing internal training, refining credential management guidelines, and reducing costs by cleaning up unused services. We believe that collaborating closely with Cremit will create valuable synergies throughout this process.
We're excited to have Cremit as a trusted partner to help secure the energy IT platform leader's journey.
Curious why Enlighten trusts Cremit to safeguard their credentials? Join them and take the first step toward securing yours!
Contact Us!.png)
Need answers? We’ve got you covered.
Below are some of the most common questions people ask us. If you can’t find what you’re looking for, feel free to reach out!
We specialize in high-converting website design, UX/UI strategy, and fast-launch solutions for SaaS and startup founders.
Helping SaaS and startup founders succeed with conversion-focused design, UX strategy, and quick deployment.
Designing sleek, user-focused websites that help SaaS and startup teams launch faster and convert better.
We design and launch beautiful, conversion-optimized websites for ambitious SaaS and startup founders.
