Stop Secrets Sprawl: Shifting Left for Effective Secret Detection
By
Felipe Araujo
November 17, 2025
5-minute read
By
Felipe Araujo
November 17, 2025
5-minute read
.png)

Speed often trumps security in fast-paced development environments. DevOps practices and CI/CD pipelines empower teams to build and deploy features at unprecedented rates, but this velocity introduces significant risks when security becomes an afterthought or a final checkpoint that's easily bypassed.
Among the most devastating vulnerabilities are leaked non-human identities. Imagine a single leaked cloud provider key granting an attacker full access to production databases – the impact can be immediate and severe. API keys, database credentials, private tokens – these sensitive pieces of information are the keys to your digital kingdom. When accidentally committed to code repositories, they create direct pathways for attackers. What's alarming is how frequently this happens, often leading to costly breaches, data theft, and permanent reputation damage.
Visualize the Software Development Life Cycle (SDLC) as a linear process:
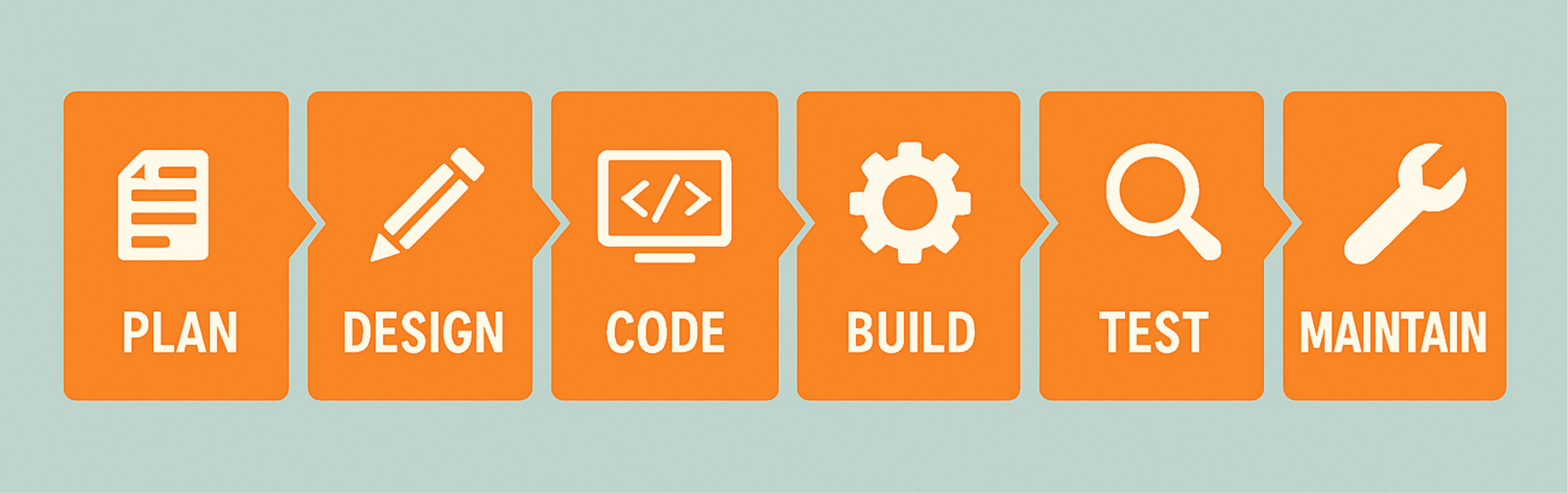
Traditionally, security testing was concentrated toward the "right" side of this timeline, often as a final gatekeeper before deployment. This approach frequently created bottlenecks, rushed security reviews, and vulnerability discoveries too late in the process to be efficiently addressed.
Shift Left Security transforms this model. Rather than treating security as a final checkpoint, it integrates security considerations throughout the development process, moving these activities "to the left" in the timeline. Security becomes an ongoing practice embedded within development rather than a separate phase.
This approach forms the cornerstone of DevSecOps – making security a shared responsibility that's automated and seamlessly integrated within the development workflow and CI/CD pipeline.
The benefits of adopting a Shift Left approach for security are compelling:
While many types of vulnerabilities exist, hardcoded secrets present unique challenges:
This combination of factors makes early and comprehensive detection absolutely essential.
Here's how to effectively apply Shift Left principles to secret detection:
Manual checks are impractical and unreliable at scale. Implement automated secret detection at multiple levels:
For successful adoption, secret detection must fit naturally into developers' workflows:
When secrets are detected, efficient remediation requires cross-functional collaboration:
Automated workflows can accelerate this process, triggering appropriate actions based on the type and severity of the exposed secret.
While detection is critical, it works best as part of a comprehensive secrets management approach:
Some security experts argue that leaked secrets are primarily an Identity and Access Management (IAM) problem rather than a code security issue. There's truth in this perspective – the ultimate fix involves revoking and rotating the compromised credential within an IAM system.
However, the complete solution requires both approaches:
The most secure organizations address both angles simultaneously, creating defense in depth.
Implementing Shift Left security for secret detection requires more than just tools:
Shift Left security for secret detection isn't just a best practice—it's a competitive necessity in today's development landscape. By integrating security early and continuously throughout the development lifecycle, organizations dramatically reduce risk while maintaining the velocity modern businesses demand.
The most successful teams recognize that speed and security aren't opposing forces but complementary goals. When security shifts left, both improve simultaneously—delivering better software, faster, with confidence that sensitive secrets remain secure.
Begin shifting your security left immediately with Cremit's comprehensive secret detection service. Experience the benefits of early and automated detection firsthand – sign up today for a free 14-day trial, or contact us to discuss how Cremit can strengthen your development process and secure your code.
.png)
Need answers? We’ve got you covered.
Below are some of the most common questions people ask us. If you can’t find what you’re looking for, feel free to reach out!
We specialize in high-converting website design, UX/UI strategy, and fast-launch solutions for SaaS and startup founders.
Helping SaaS and startup founders succeed with conversion-focused design, UX strategy, and quick deployment.
Designing sleek, user-focused websites that help SaaS and startup teams launch faster and convert better.
We design and launch beautiful, conversion-optimized websites for ambitious SaaS and startup founders.
