Introducing Probe! Cremit's New Detection Engine
Probe detects exposed credentials and sensitive data across cloud tools, automating validation and alerts, with AI-powered scanning for enhanced security.

The challenges of managing credentials
Non-Human Identities such as API keys and passwords are essential for accessing services in modern, cloud-based, and collaborative work environments. Yet, as employees often store these credentials in easily accessible places (like code repositories, messengers, and cloud documents) to boost work speed, the risk of exposure has grown, leading to high-profile breaches at companies like Okta, Microsoft, Uber, and CloudFlare.
To address this, tools like TruffleHog and GitGuardian have emerged. TruffleHog, an open-source solution, scans source code and collaboration platforms using regex patterns to validate different credential types. However, its reliance on preset patterns limits its ability to detect new credential types or sensitive information beyond its scope, and it only scans one source at a time. GitGuardian, a SaaS-based service, provides real-time alerts and reporting across various cloud products but struggles with scalability and customization—especially when detecting personally identifiable information (PII). These limitations set the stage for a more robust secret detection solution.
Introducing Probe
A probe is a spacecraft designed to explore space and collect data on planets, moons, and asteroids. Similarly, Probe is our product that explores the cloud to detect exposed credentials. Unlike existing solutions, Probe overcomes key limitations to deliver comprehensive security. Key features include:
- Support for Multiple Collaboration Tools
Probe scans source code repositories and various collaboration tools like Slack, Jira, Confluence, and Notion. This ensures comprehensive detection of credential exposure risks across day-to-day workflows, not just during development. - Broad Credential Detection and Validation
Probe detects 800+ types of credentials and automatically validates their validity. This reduces false positives, allowing security teams to focus on genuine threats. - Multi-Source Scanning
Probe can simultaneously scan and validate credentials across multiple sources. This capability ensures efficient detection and validation, even for large organizations. - AI-Powered Sensitive Data Detection
Beyond credentials, Probe leverages AI to detect sensitive data such as Personally Identifiable Information (PII). By using models optimized for natural language and code analysis, Probe achieves high accuracy in detection. - Dashboard and Alerting Support
Probe features an intuitive web dashboard for tracking credential detection status. It also provides real-time notifications via Slack, Telegram and other messengers, enabling quick responses to potential issues.
Probe’s features help overcome the limitations of traditional credential detection tools, with advanced credential verification, AI-powered sensitive data detection, and multi-source scanning, taking your security to the next level.
Probe also delivers significant performance advantages over other products. Speed is critical for responding quickly to credential exposure threats. Built in Rust, Probe leverages efficient string search algorithms and advanced optimizations to detect credentials swiftly, even in large datasets.
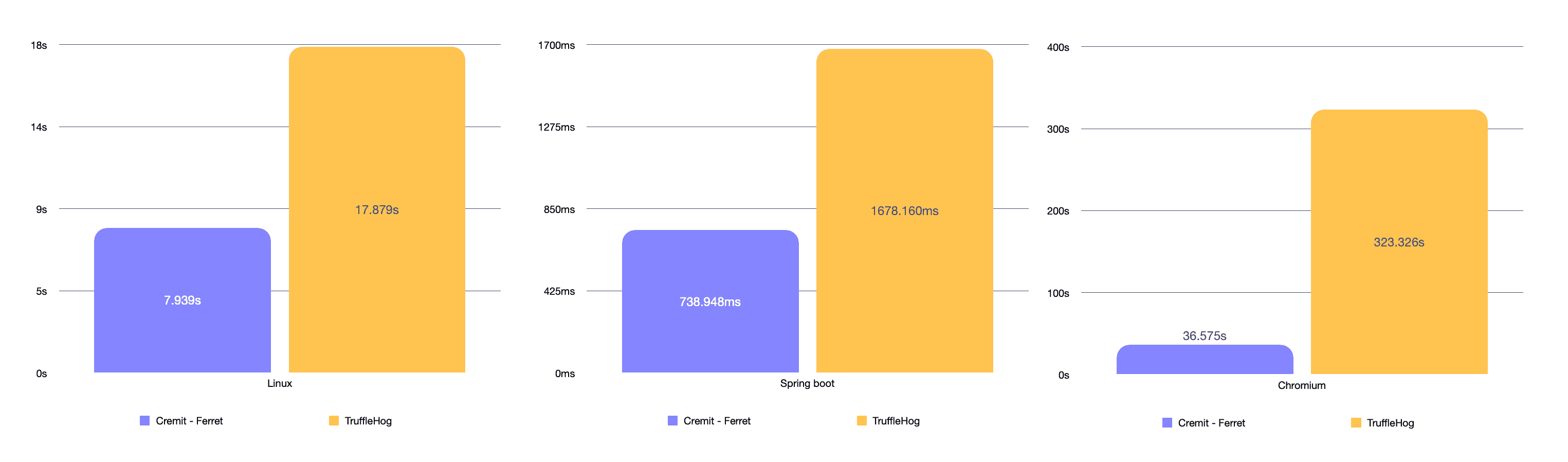
Probe significantly outperformed TruffleHog in scan speed across various environments, including Linux, Chromium, and Spring Boot. On average, Probe was 2x faster when scanning codebases and up to 8.8x faster for large projects like Chromium. This enhanced speed enables faster responses to credential exposures and greatly improves the efficiency of credential detection in large organizations.
Future Plans
Probe is continually evolving to deliver even greater value to our customers. Here’s what’s coming next:
- Expanded Support for Collaboration Tools and Detection Types
While Probe already supports a wide range of tools, we plan to include more cloud collaboration platforms, enabling customers to adapt Probe to their unique workflows. Additionally, we aim to extend detection capabilities to cover credentials in non-text data, such as images. - Custom Detection and Validation Rules
Probe will allow users to define specialized credential detection and validation rules, such as identifying internal usernames and passwords. This flexibility will improve scalability and security for organizations with unique needs. - Credential Metadata Collection and Management
New features will enable the collection and utilization of credential metadata to assess exposure scope and threat levels. This will streamline credential management for security teams and enhance efficiency. - AI Model Diversification and Performance Improvements
We plan to further diversify Probe’s AI models and enhance their performance, delivering more accurate and versatile detection of sensitive data. - Automatic Credential Action Capabilities
To respond swiftly to breaches, Probe will develop features to automatically change or deactivate exposed credentials, ensuring quick and effective mitigation. - Credential Archiving and Usage
Probe will provide secure storage and seamless management of detected credentials, enabling organizations to handle the entire credential lifecycle within Cremit.
Let's Get Started
Cremit offers both SaaS and On-Premise (Enterprise) solutions optimized for startups, small businesses, enterprises, and finance sectors. With support for 800+ secret validations, NER-based privacy detection, and integrations for source code, collaboration tools, documents, and repositories, we empower organizations to enhance their security posture.
(/contact-us)
